Hi Everyone,
In this article, I will take you through common cryptography terminologies and what they mean.
Cipher
An encrypted message is called a cipher. Encryption techniques are helpful in maintaining secrecy.
Example:
- Plaintext: David is the traitor
- Key: shift each letter by '2' letters in alphabetical order. ('a' becomes 'c')
- Cipher: Fcxkf ku vjg vtckvqt
Encryption and Decryption
The process of converting 'readable' plaintext into a 'non-readable' ciphertext is called encryption, and the reverse process is called decryption.
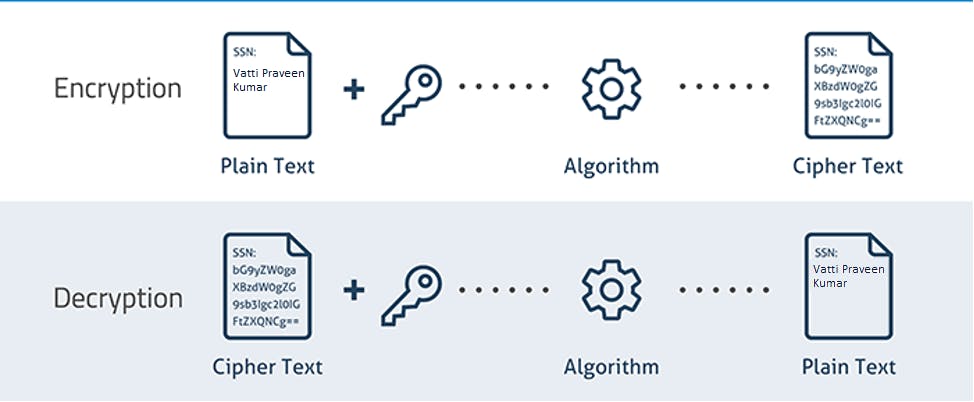
A 'Key'(data) is used to encrypt/decrypt.
There are 2 types of encryption algorithms:
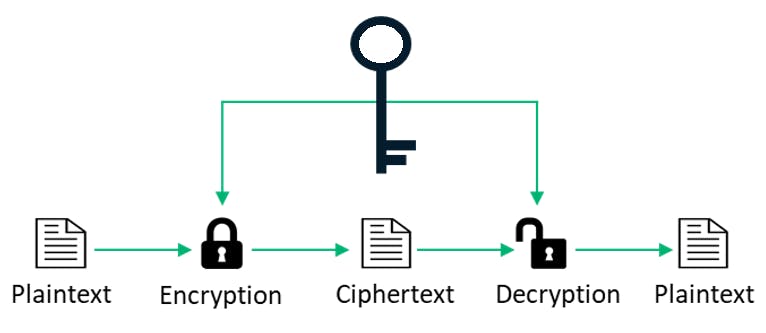
Symmetric-key algorithms
- A single key is used for both the encryption of plaintext and decryption of ciphertext.
- Examples: DES(Data Encryption Standard), AES(Advanced Encryption Standard).
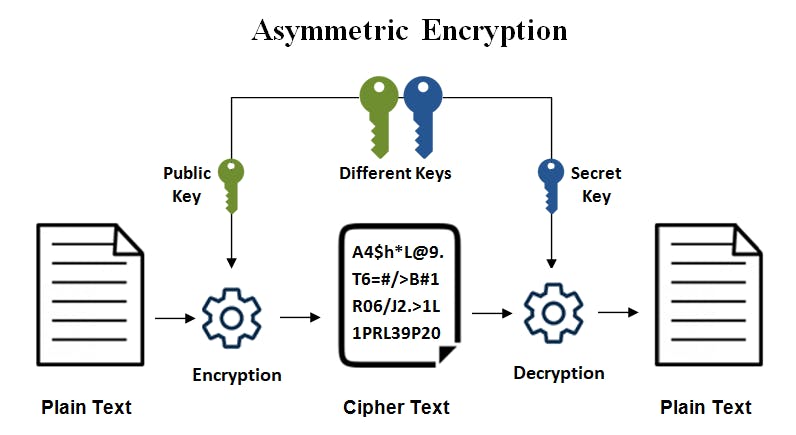
Asymmetric-key algorithms (Public-key algorithms)
- A pair of related keys(Private and Public keys) are used. One for encryption and the other for decryption.
- The public key is out in the open for everyone to see. Whereas the private key must be kept secret and not shared with anyone.
- If someone encrypts a message/plaintext using A's public key (available for everyone), only A can decrypt the ciphertext using A's private key.
- Similarly, If A encrypts a message/plaintext using his/her private key, anyone can decrypt the ciphertext using A's public key(available for everyone).
- Examples: RSA(Rivest Shamir Adleman), ECC(Elliptical Curve Cryptography).
Symmetric-key algorithms are computationally faster than Asymmetric-key algorithms.
Hashing
Hashing is a one-way message digestion process of any varied-length input to a fixed-length output(Hash/digest). Hashing techniques are helpful in validating data integrity.
- It is one-way, as it is almost impossible to recover the original message from the hash value (unlike encryption algorithms, where cipher can be decrypted).
- Hashing algorithms are computationally super fast.
- Deterministic: meaning for a given input, the algorithm gives the same output every time it is run.
- Avalanche effect: Even a small change in the input drastically changes the output (hash value).
- A good hashing algorithm should withstand collisions. (since there will be collisions when larger varied length inputs are hashed to small fixed-length outputs EX: (13 mod 9) = 4 and also (85 mod 9) = 4).
- Examples: MD5, SHA-1, SHA256
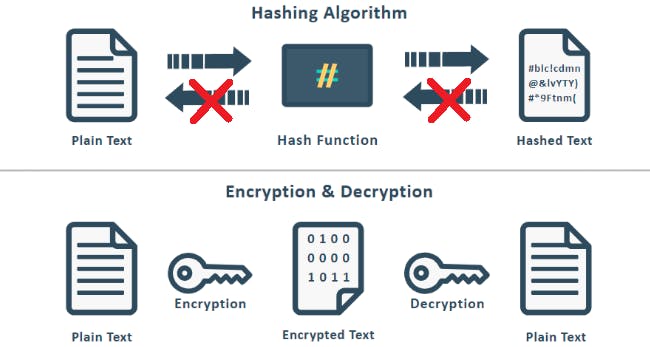
These properties are important in understanding why hashing plays a vital role in creating Blockchains
Digital Signatures
Just like signatures are helpful in verifying the authenticity, Digital signatures are useful in verifying the authenticity of the author/sender of the document/message. Hashing and Asymmetric-key(public key) algorithms are used in creating and verifying digital signatures.
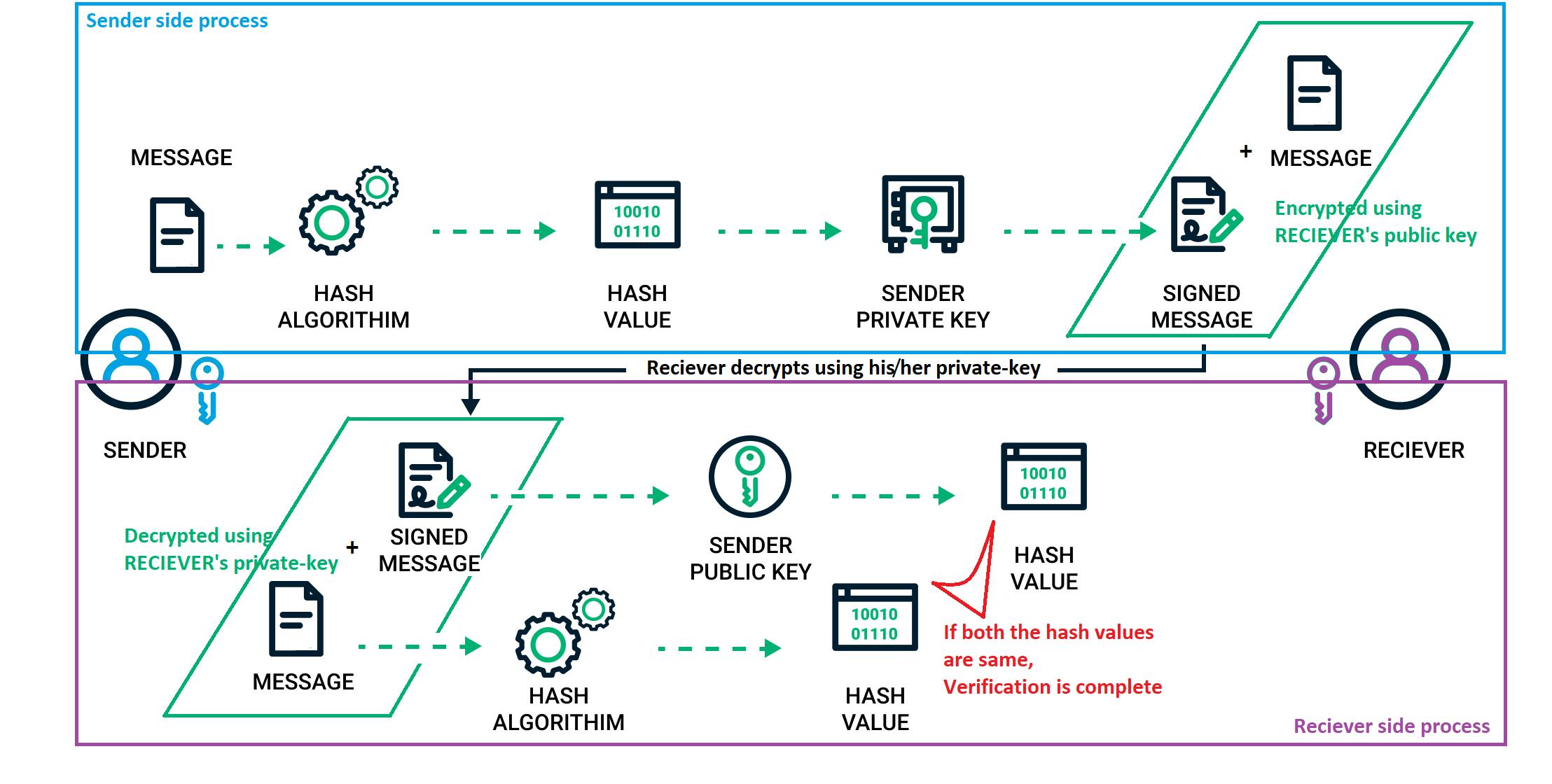
Sender(S):
- S wants to send Message(M) to the receiver(R). Hash of message(M) -> Hs is generated.
- Hash(Hs) is encrypted(Es-Hs) using Sender's private key.
- Both (Es-Hs & M) are together encrypted(Er-(Es-Hs & M)) using Reciever's public key.
Receiver(R):
- R decrypts the (Er-(Es-Hs & M)) using his/her private key. -> Es-Hs & M.
- R now generates a hash of message(M) -> Hr
- R decrypts (Es-Hs) using sender's public key -> Hs
- If (Hr == Hs) then, the sender's authenticity is verified.
Digital signatures are used in Blockchain networks. Wallets store private keys and the public keys(address) are shared over the blockchain network.
Homomorphic Encryption Algorithms
Homomorphic algorithms are helpful in implementing operations on the cipher and still achieve the result same as some operations performed on the plaintext and then encrypted.
Example:
- Say, A, and B are variables that store plain text.
- Encryption Algorithm: Cipher of A be (g^A) and Cipher of B be (g^B).
- Decryption Algorithm: log(g^A) = A (base of log operation be 'g').
- On performing multiplication operation -> (g^A ) * (g^B) = (g^(A+B)) -> This is similar to perfoming addition (+) operation A and B and then encrypting it.
This feature is useful when the cipher is stored in a cloud environment (untrusted service providers can't view data) and the user can still perform operations without decrypting the cipher.
Salts, Nonces
These are one-time values used in cryptography that don't need to be secret but still lead to additional security.
Salt: Salt is used in password-based systems and is concatenated to the front of a password before processing, making it difficult for hackers to guess the password. Nonce: Number used once. A nonce is a random number, used in cryptographic protocols and algorithms, it should only be used a single time with any particular cryptographic key.
Please do advise improvements and suggestions, helps me in making better content in the future. Thank you for reading. Have a great day.😎

